🚀 Check out this awesome post from Hacker News 📖
📂 **Category**:
✅ **What You’ll Learn**:

Israeli surveillance company Paragon Solutions briefly exposed its own spyware dashboard on LinkedIn, revealing the hidden architecture of a billion-dollar surveillance empire built on the backs of journalists, activists, and ordinary people.
The technical slip-up is a moment of rare transparency in an industry built on secrecy, exposing the operational interface used to compromise devices, intercept communications, and harvest data from targets worldwide.
The $900 million acquisition of Paragon by U.S. private equity firm AE Industrial Partners tells you everything you need to know about who profits from your digital insecurity. Former Israeli Prime Minister Ehud Barak reportedly pocketed $10-15 million from the deal, a tidy sum for a politician-turned-surveillance capitalist.
What the LinkedIn photos show is chilling: a Czech phone number labeled “Valentina,” interception logs marked “Completed,” and application-level data categories targeting encrypted services. This isn’t some theoretical cybersecurity threat, it is the real-time dashboard of the modern surveillance capitalism system we endure.
John Scott-Railton, a senior researcher at the University of Toronto’s Citizen Lab, described the disclosure as an “epic OPSEC fail,” highlighting how the operational-security discipline on which the commercial spyware industry depends had been violated.
Paragon’s flagship product, Graphite, represents the cutting edge of what researchers call “mercenary spyware”— highly targeted intrusion systems sold exclusively to state agencies. Unlike conventional malware, these platforms are engineered for precision, using zero-click exploit chains that compromise devices without any action from the target.
Once installed, spyware operates at the operating-system level, granting operators visibility into:
-
Stored data and communications
-
Microphone and camera activation
-
Enclosed applications and services
-
Messages accessed before encryption or after decryption
The secure boundaries that millions rely on including encrypted chats, locked apps, protected accounts dissolve once the device itself is compromised. Even if Paragon executives call this “lawful access”, we all know there is nothing lawful about accessing someone’s entire digital life without their knowledge or consent?
After NSO Group’s Pegasus spyware generated global outrage by targeting journalists and dissidents, Paragon tried to position itself as the “ethical” alternative—a “light-touch” approach operating “within apps” rather than compromising the entire device.
Independent researchers at Citizen Lab have repeatedly debunked this distinction. Once spyware achieves device-level persistence, access pathways inevitably extend beyond the narrow confines vendors claim and describe.
The technical reality is clear: if you can compromise a device, you can access everything.
Laws and court precedents consider full device compromise as extraordinarily invasive, creating strict legal requirements. By describing their capabilities as ‘selective’ rather than ‘systemic,’ spyware vendors strategically frame their intrusion as less severe to navigate around these legal barriers and avoid meaningful oversight.”
Applications like WhatsApp are widely understood as privacy-preserving technologies. End-to-end encryption, Meta has long argued, ensures that only communicating users can read messages or access calls. For hundreds of millions of people, that assurance functions as a baseline assumption of digital safety.
Disclosures over the past year have repeatedly unsettled that belief.
In early 2025, Meta notified roughly 90 WhatsApp users that their devices had been targeted with spyware linked to Paragon. The victims reportedly included journalists and members of civil society—individuals whose communications are often politically sensitive and professionally vulnerable.
Researchers have emphasized that infections associated with mercenary spyware frequently occur without user interaction. There are no malicious links to click, no suspicious files to download. Devices are compromised through exploit chains operating below the threshold of ordinary detection.
The episode reinforced a reality digital security researchers have warned about for years: encryption protects communications in transit, but offers limited protection once the device itself has been compromised.
The $900 million valuation of Paragon Solutions reveals the brutal economics of surveillance capitalism. Remote device intrusion is immensely profitable. When government clients create the demand, and private equity investors drive the scale, the revolving door between state security and commercial surveillance becomes the engine that powers this industry. Former senior officials and intelligence veterans populate executive ranks, repackaging capabilities developed for national security into commercial products.
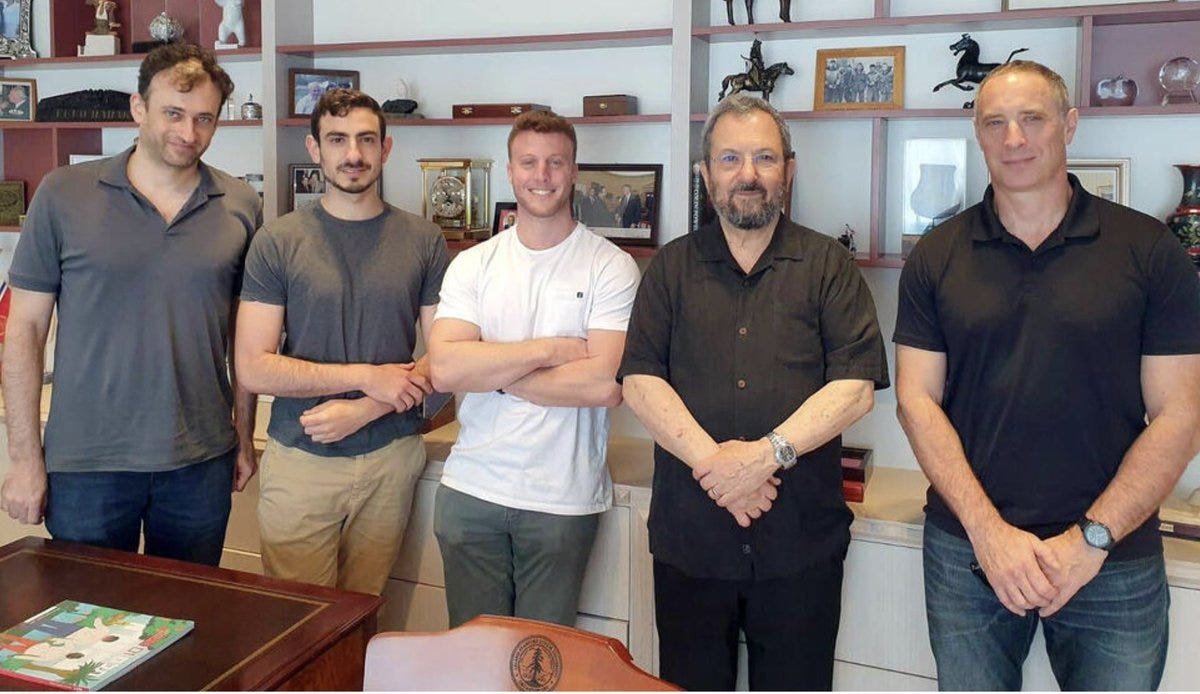
Paragon’s founding team not includes the former Israeli PM Ehud Barak, it also includes former Unit 8200 commander Ehud Schneorson, exposing how Israeli intelligence expertise metastisizes into private markets. The same skills used to monitor Palestinians in the occupied territories are now being sold to governments worldwide.
Israeli-made Pegasus spyware has been licensed to roughly 45 governments worldwide, including at least 5 to 14 European Union states, turning a tool sold for “national security” into one of the most pervasive government surveillance systems on Earth, according to Citizen Lab.
Israel has become the Silicon Valley of surveillance technology over the past two decades. A dense network of private firms operates alongside military and intelligence institutions, with personnel pipelines flowing between state security structures and commercial ventures.
Palestinians have long lived under one of the most extensively documented surveillance regimes in the world. The deployment of facial recognition systems, predictive analytics, and device monitoring technologies in the occupied Palestinian territories are widely documented by human-rights organizations and digital researchers.
At the same time, U.S. immigration enforcement agencies are expanding their own technological arsenal—biometric databases, algorithmic risk scoring, location tracking, and now, potentially, advanced spyware capabilities using the same institutional logics are identical: Identify. Track. Classify. Control.
What was developed to control Palestinians in occupied territories is now sold to control immigrants in America. The same surveillance infrastructure built under occupation becomes a commercial product sold to authoritarian regimes worldwide.
While the political contexts differ, the technologies increasingly circulate within overlapping global markets. The actors shaping this ecosystem include former heads of state, elite intelligence veterans, multinational investors, and government clients.
Public procurement records reveal that U.S. immigration enforcement agencies have engaged with Paragon’s Graphite technology, including contracts with DHS and ICE. While the exact procurement process remains obscured in bureaucratic paperwork, the fact that ICE—an agency notorious for due process violations, detention conditions, and aggressive enforcement practices—secured advanced Israeli spyware capabilities speaks volumes about where the Trump administration’s priorities truly lay.
The Trump administration is expanding the surveillance state’s reach into the lives of immigrants and marginalized communities, using the most invasive tools available from the Israeli surveillance industry.
Spyware companies consistently invoke crime prevention and national security in their public messaging. But follow the money, and the real story emerges: extraordinary valuations are commanded by companies capable of defeating device security because governments continue purchasing those capabilities.
We live in an age of unprecedented surveillance, where the architecture of control is built not just with walls and checkpoints, but with algorithms and exploits. The same logic that governs the occupied territories now governs our digital lives, sold to us as progress and security.
Paragon’s moment of transparency showed us the face of modern surveillance capitalism. The irony is bitter: the same people who built the surveillance state now profit from selling its tools to the highest bidder. Their fortunes are built on the erosion of privacy, the compromise of security, the violation of digital sanctuary. We are told this is about national security, about fighting terrorism. But follow the money, and the truth emerges: this is about power. This is about control. This is about the commodification of human vulnerability.
The devices in our pockets are no longer just tools. They are also windows, and mirrors. They are the architecture of our own surveillance, sold to us as convenience, packaged as security, and monetized as data.
Paragon exposed itself not through negligence, but through arrogance and the belief that their work was so normalized, so institutionalized, that it could be displayed openly on a professional networking site.
And in that moment of exposure, we saw the truth: the surveillance industry operates not in shadows, but in plain sight. The only thing hiding its true nature is our own willingness to look away, our own complicity in the fiction that this is somehow about security rather than control.
The surveillance industry does not just compromise our devices. It compromises our humanity. And that is the ultimate cost of this billion-dollar empire.
The threat is global and immediate. The tools developed in Israel to surveil and control Palestinians are now in the hands of ICE to surveil and control immigrants in America. They are in the hands of authoritarian regimes worldwide to surveil and control their citizens. They are in the hands of corporations to surveil and control consumers.
This is the new colonialism, executed not through armies and occupation, but through algorithms and exploits. The same institutional logic that justified the occupation of Palestinian territories justifies the occupation of our digital lives. The same people who profited from one occupation now profit from the next.
When former intelligence chiefs and politicians sit on corporate boards and rake in millions from the surveillance industry, when governments purchase these tools without democratic debate, when the media fails to connect the dots between occupation and digital control—this is the conspiracy.
The dissent that was once silenced in Gaza is now being erased in our inboxes. The journalists who were targeted in the occupied territories are now being targeted in our own cities. The activists who were monitored in refugee camps are now being monitored in our communities.
This is a crisis of global proportion, a threat to human dignity that crosses borders and transcends politics. The question is no longer whether we should be concerned about surveillance. The question is whether we will allow this system to continue unchecked, whether we will demand accountability from those who profit from our vulnerability, whether we will reclaim our digital lives from those who would turn our devices into tools of control.
{💬|⚡|🔥} **What’s your take?**
Share your thoughts in the comments below!
#️⃣ **#Israeli #Spyware #Firm #Accidentally #Exposed**
🕒 **Posted on**: 1771250313
🌟 **Want more?** Click here for more info! 🌟




