🔥 Discover this insightful post from Hacker News 📖
📂 **Category**:
💡 **What You’ll Learn**:
After being interrupted multiple times by an annoying console window that would pop up periodically on my new gaming PC, I managed to track the offending executable down to AMD’s AutoUpdate software.
In my anger, I decided to punish this software by decompiling it to figure out how it worked, and accidentally discovered a trivial Remote Code Execution (RCE) vulnerability in the process.
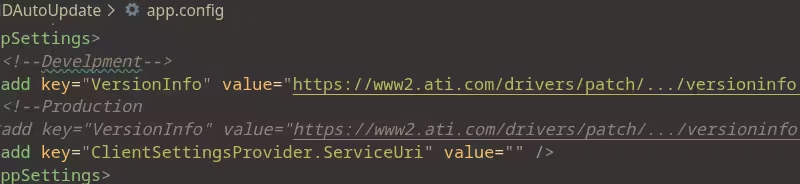
The first thing I found, is that they store their update URL in the program’s app.config, although its a little odd that they use their “Develpment” URL in production, it uses HTTPS so its perfectly safe.
The real problem starts when you open up this URL in your web browser, and realise that all of the executable download URL’s are using HTTP.
This means that a malicious attacker on your network, or a nation state that has access to your ISP can easily perform a MITM attack and replace the network response with any malicious executable of their choosing.
I was hoping that AMD perhaps had some form of certificate validation to ensure that it could not download & run any unsigned executables, however a quick look into the decompiled code revealed that the AutoUpdate software does no such validation and immediately executes the downloaded file.
After finding this issue, I thought it was worth reporting to AMD since it seemed to be a pretty severe issue.
However it turned out to be considered “out of scope”, resulting in AMD not considering this to be a vulnerability.
Timeline (DD/MM/YYYY)
- 27/01/2026 – Vulnerability Discovered
- 05/02/2026 – Vulnerability Reported
- 05/02/2026 – Report Closed as
wont fix/out of scope - 06/02/2026 – Blog published
If you liked this blog, you can read another of my write-ups here: 1.4 Billion exposed user records via insecure Firebase instances in top Android apps
💬 **What’s your take?**
Share your thoughts in the comments below!
#️⃣ **#RCE #AMD #wont #fix**
🕒 **Posted on**: 1770340453
🌟 **Want more?** Click here for more info! 🌟